How to Identify and Prevent Phishing Attacks
Phishing is one of the most common and effective forms of social engineering. Attackers use various methods, including email, voice, and text messages (SMS), combined with personal details they learn from publicly available sources to get their targets to give out sensitive information or access to funds. One of the best ways you can prevent becoming a victim of phishing is to learn about exactly what it is and how it is executed.
What is phishing?
Phishing is when an attacker sends emails pretending to someone else to gain personal or company information, like passwords and credit card numbers. Before we talk about ways to prevent phishing, let’s cover some common different types of these attacks.
Generic Phishing
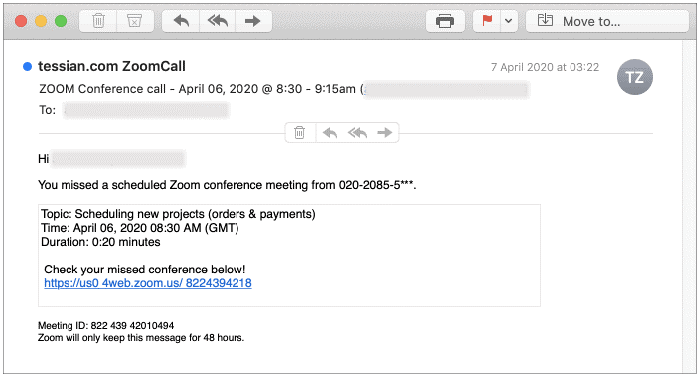
The simplest form of phishing is when an attacker gathers as many emails as they can from the target organization and uses all of them in their attack. The attacking email will look generic in this case, but it will contain contents that an average user may believe.
In this example, the link that claims to be to the missed conference is malicious. The attacker’s goal is to get the target to click that link.
Spear Fishing
Spear phishing is when an attacker either gathers specific emails pertaining to certain roles in an organization or targets one specific person’s email.
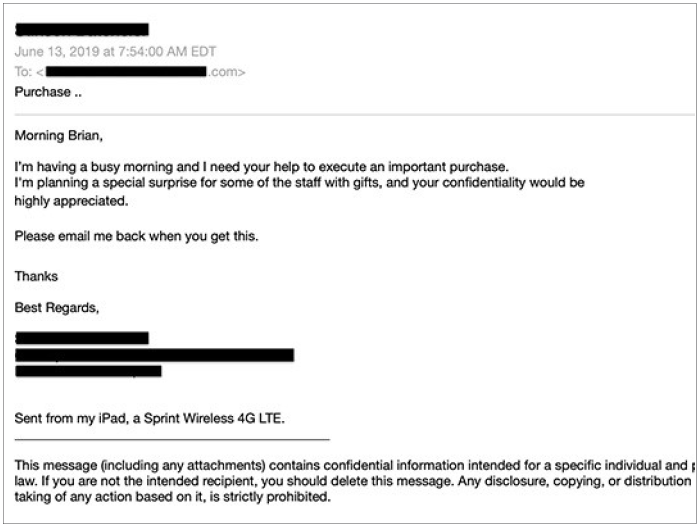
In the event of a specific person, the attacker may have found relevant and unique information pertaining to an individual. For a small group, the attacker may target users that are on a team or in the same department of an organization, such as accounting, sales, customer service, etc.
In the spear phishing example below, the attacker has focused on a front desk staff member or an administrative assistant (spoofed to appear to be the person’s boss or another individual at their organization).
Whale Phishing
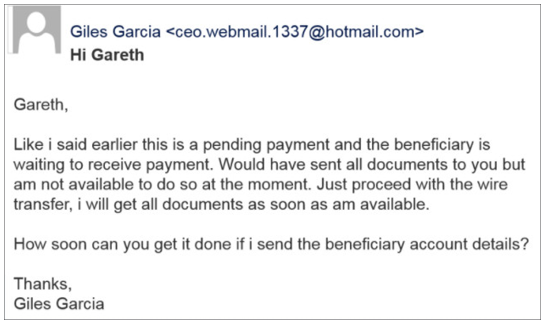
Whaling is like a spear phishing attack, except it focuses on targeting high-level management within the organization. One of the most common attacks is attempting to get a wire transfer.
Vishing
Vishing is the act of phishing via telephone (voice) instead of email. The attacker will call a victim to verify pieces of information from the victim, such as email or phone number. The attacker uses the data they already know to gain rapport on a call and ask for more sensitive information. For example, the attacker may claim to be a third-party IT vendor and, after verifying some of the victim’s information, may ask for details about the workstation, or even have the user install remote control software.
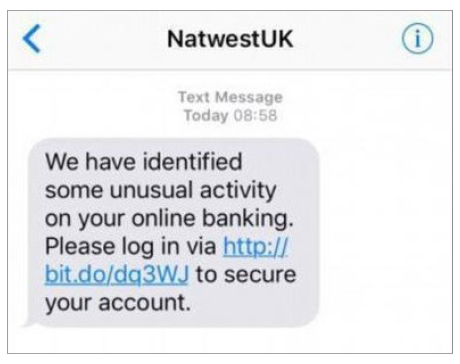
SMS Phishing
Attackers can send your mobile device a text message with a seemingly urgent message – a package cannot be delivered until it is confirmed, a streaming account will be canceled if you don’t click this link and confirm, etc. – or a promise of money or an enticing prize.
Once the target clicks the link it may load malware directly onto their device. The user may also be taken to a spoof page where they enter their credentials or payment information, which are then sent to the attacker.
How to Identify a Phishing Attack
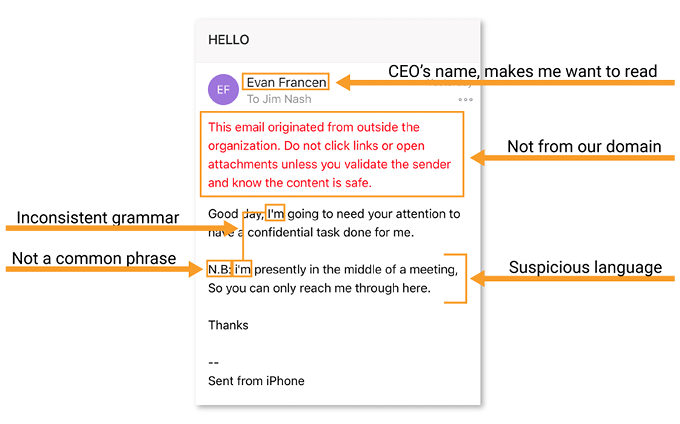
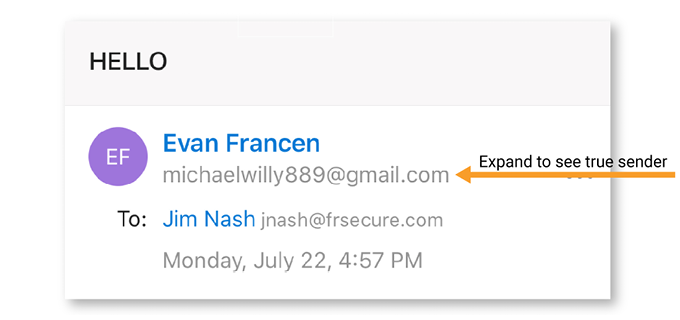
Phishing relies on perceived urgency and emotional response, but if you train yourself to check a few things before blindly obeying, you should increase your odds of evading a trap. In the example below, the email address that should be Evan’s belonged to a scammer sending from michaelwilly889@gmail.com. This simple habit of clicking or expanding the box around the sender’s email name to reveal the email address can help you uncover if the person sending the email is who they claim to be.
How to Protect Yourself Against Phishing Attacks
Training
First and foremost, train yourself and your team. Educate your users on how to identify phishing emails and what to do when they receive them. Below are some starting points to educate on, look for, or to be wary of:
- Does the domain look suspicious? Is the domain missing a character, or are there extra characters? Are any of the characters replaced with another character?
- Inform users about the dangers of sharing personal information on social media sites. The more the attacker can learn, the more information they can use against the user when crafting phishing emails, specifically spear phishing.
- Encourage your users to speak up if they see anything suspicious. Spelling mistakes, suspicious links or attachments, a generic greeting, requests to log in, or requests to give your password are all forms of suspicious requests or behavior.
- Let your employees know that you would much prefer they report clicking a phishing link than an incident response investigation later. Additionally, tell your users that if they are unsure of an email, they can send it to an IT email to verify the legitimacy.
- In the case of vishing attacks have a codeword or phrase to verify the caller’s identity. If the caller can’t reproduce this word or phrase, report the call to either IT or management.
- Establishing policies and procedures about who resource owners are can put users at ease in the event of a spear phishing email or even a vishing call. If the user knows who to expect specific requests from, they may be less likely to share information or do tasks they weren’t expecting to be requested of them from that person.
- Conduct phishing exercises to track progress and verify that your users are learning effectively. There are platforms available to simulate a phishing attack. Conducting these exercises allows you to set a benchmark and track your results over time to show success or areas of improvement.
Multifactor Authentication
While training helps, it isn’t a silver bullet. When a user clicks on a link and potentially has their password compromised, multifactor authentication (MFA) can prevent the entire account from being compromised. MFA can be in the form of an SMS text message, push-button notifications, an authentication app, or a physical token with a changing code. Many organizations use Office365. Use this document to help you get started setting up multifactor authentication in O365.
Perform Reconnaissance
One of the best steps you can take to assess your risk is to understand your internet presence and that of your users. This will help identify vulnerabilities to remedy and will allow you to see what the attackers are likely able to see. With this knowledge, you will be able to protect your organization better.
There are many ways to go about this and tools available to do this, but we recommend using Discover. Discover is a tool that uses several other tools to perform various reconnaissance searches. It will search social media sites, multiple search engines, DNS lookups, and several other valuable sources of information to see what is publicly available about the specific company name and the company’s domain. Types of information it finds can include emails, employee names and job titles, files hosted on the domain searched, subdomains, and more.
Identify and Disclose Incoming External Emails
Another valuable tool in your phishing prevention toolbox is giving your users the immediate ability to easily recognize when an email originated outside of your organization. You can add a statement at the top of all incoming external emails stating that they came from outside of your organization.
This helps users know when they are viewing potentially malicious emails. This is especially helpful when attackers attempt to appear as though they are a colleague; the notice will quickly alert the recipient that the sender is not who they claim to be.
This blog was contributed by FRSecure. FRSecure is a full-service information security management company that protects sensitive, confidential business information from unauthorized access, disclosure, distribution, and destruction. View our free cybersecurity webinar with FRSecure here. Learn more about phishing and cybersecurity by signing up for Choice’s Taking Care of Business Webinar email list, here.
Being in the know is the first step to protecting yourself and your business from cyber fraud. Choice Bank is committed to providing you with up-to-date resources and tips to help you stay informed. Learn more at bankwithchoice.com/cybersecurity.



